How to Check Database Encryption in SQL Server? Step-by-Step Guide
Database encryption in SQL Server refers to encrypting data stored in a SQL Server database to protect it from unauthorized access. Encryption gives an extra layer of assurance by changing over information into an unreadable organize, rendering it futile to unauthorized people even if they pick up and get to the database.
In this article, we’ll dig into the fundamental methods and strategies to check database encryption in SQL Server, enabling administrators and database experts to maintain information secrecy and brace their information against potential dangers. The following steps outline the procedure for checking the encryption status of a database in an SQL server.
Understanding Database Encryption in SQL Server
SQL Server is a widely used RDBMS designed by Microsoft for storing, managing, and retrieving vast amounts of structured data.
Its database encryption ensures data security by converting sensitive information into an unreadable format using cryptographic algorithms, making unauthorized access impossible without the decryption keys.
Transparent Data Encryption (TDE)
TDE encrypts the entire database at rest, making data inaccessible without the encryption key. Files on disk are encrypted, ensuring data confidentiality and security.
Cell-level Encryption
SQL Server’s column-level encryption enables encrypting specific sensitive columns while leaving other non-sensitive data in plain text. It allows for securing critical information like credit card numbers or social security numbers selectively.
Always Encrypted
Always Encrypted in SQL Server enables client applications to encrypt sensitive data before sending it to the database and decrypt it upon retrieval. Encryption and decryption occur on the client side, ensuring the database never accesses unencrypted data.
Backup Encryption
SQL Server permits you to encrypt database backups to ensure the information in case the backup records are compromised.
SSL Encryption
SQL Servers use SSL (Secure Sockets Layer) encryption for secure communication between client applications and the database server, ensuring data transmitted over the network is encrypted.
Methods to Check Database Encryption in SQL Server
To check database encryption in SQL Server, you can use different methods depending on the type of encryption you want to verify. Below there’s a generalized procedure followed by a couple of methods- to check Transparent Data Encryption (TDE) and Always Encrypted.
Step-by-Step Generalized Guideline
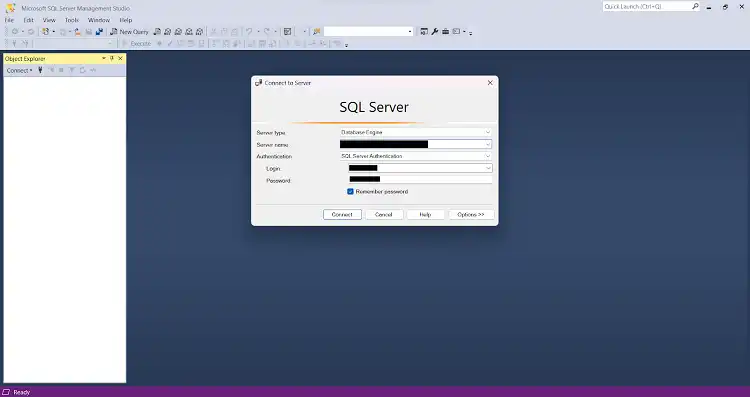
Step 1: Open SQL Server Management Studio (SSMS) application and connect to the SQL server using the appropriate credentials.
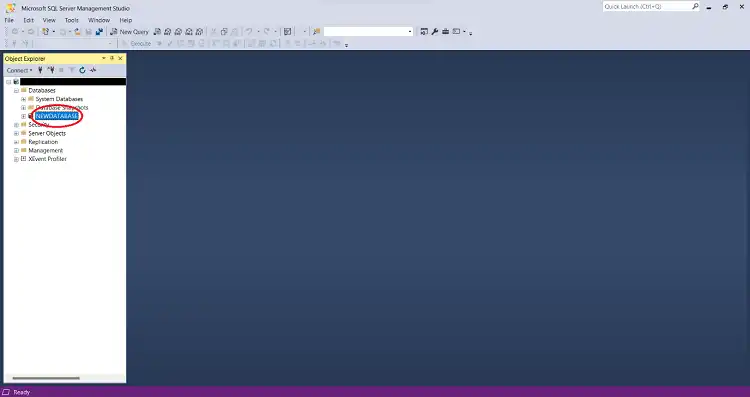
Step 2: In SSMS, expand the “Databases” folder to see a list of databases.
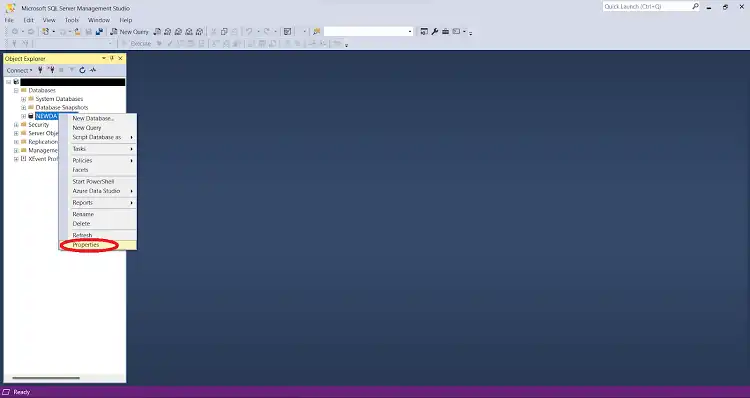
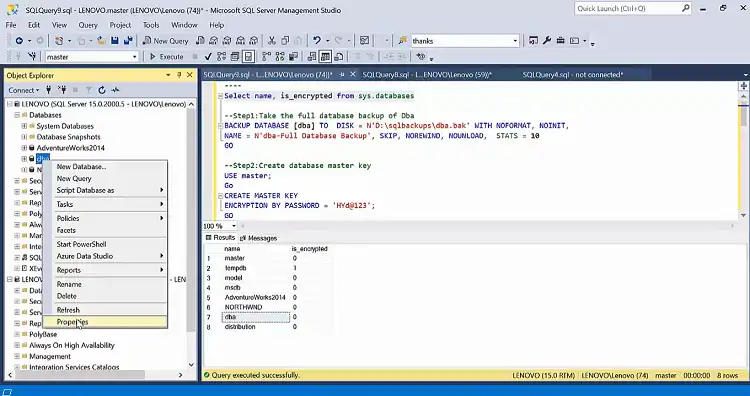
Step 3: To check a database’s encryption, right-click on it and choose “Properties” from the context menu.
Step 4: In the Database Properties window, navigate to the “Options” page on the left-hand side.
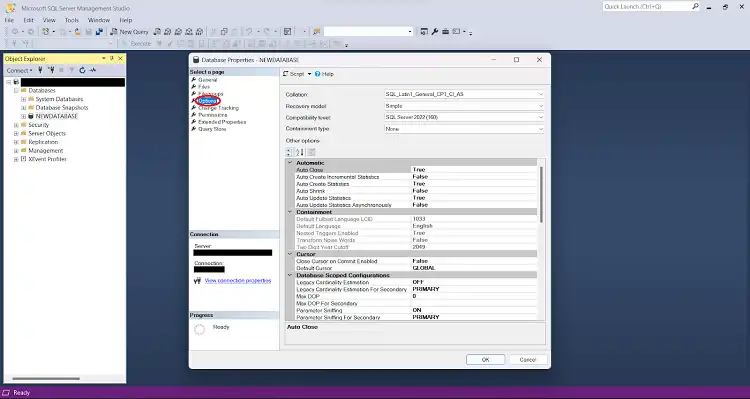
Step 5: Scrolling down “Encryption Enabled” property will be found. If it says “True,” it means the database is encrypted. If it says “False,” the database is not encrypted.
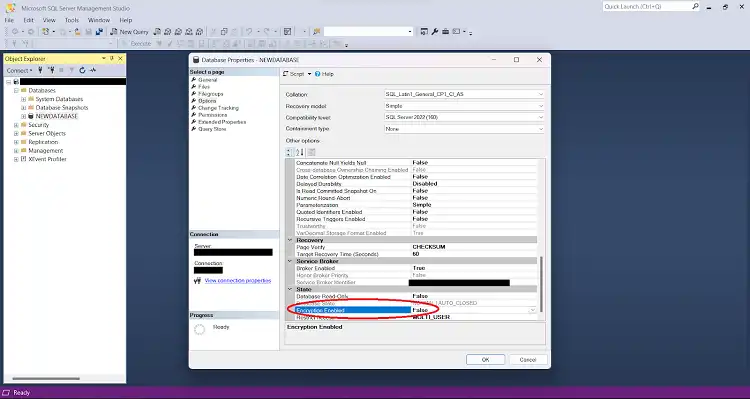
Step 6: If the database is encrypted, further check the encryption status of individual database files by looking for the “Encryption State” property under the “Files” section on the same “Options” page. If it shows “2,” the file is encrypted with a database encryption key. If it shows “0,” the file is not encrypted.
Step 7: Additionally, check the encryption algorithm used for TDE by looking at the “Encryption Algorithm” property under the “Files” section, which shows the encryption method used, such as AES or Triple DES.
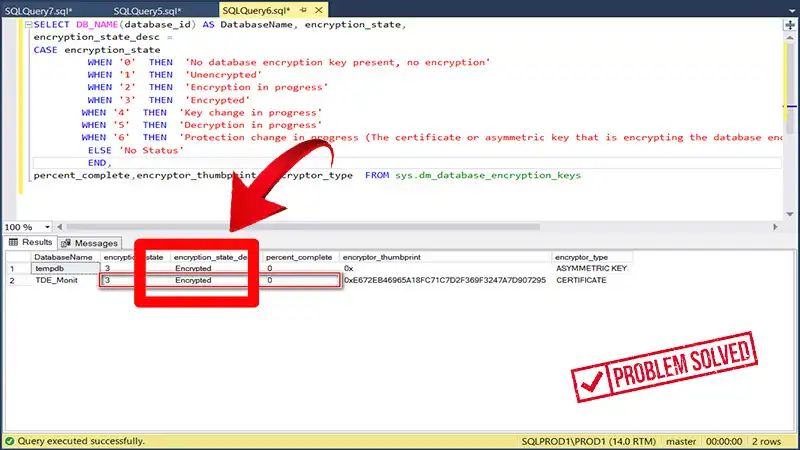
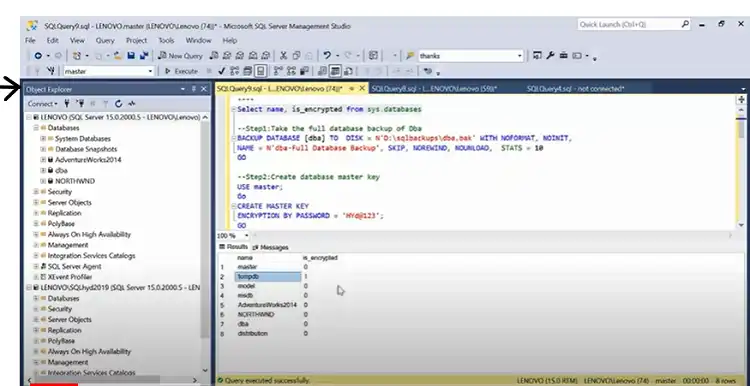
Step 8: Check the encryption status of all databases on the SQL Server instance using the following T-SQL query:
SELECT name, is_encrypted FROM sys.databases;The query will display a list of databases and whether they are encrypted (1 for encrypted, 0 for not encrypted).
Step 9: Click “OK” to close the Database Properties window.
By following these steps, determine if the SQL Server database is encrypted using Transparent Data Encryption (TDE) and view the encryption status of individual database files.
Checking Transparent Data Encryption (TDE)
Method 1: Using SQL Server Management Studio (SSMS)
Step 1: Use the proper credentials to log in to SQL Server Management Studio (SSMS).
Step 2: To see a list of the databases on the server, expand the “Databases” node in the Object Explorer.
Step 3: To examine a database’s encryption, right-click on it and choose “Properties.”
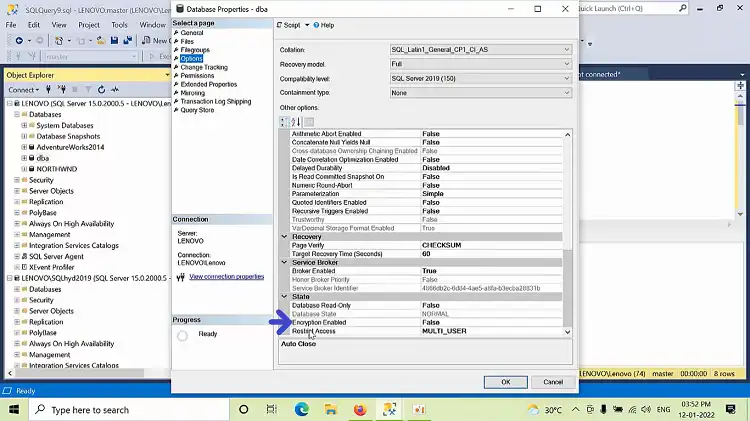
Step 4: Navigate to the “Options” page on the left side of the Database Properties window.
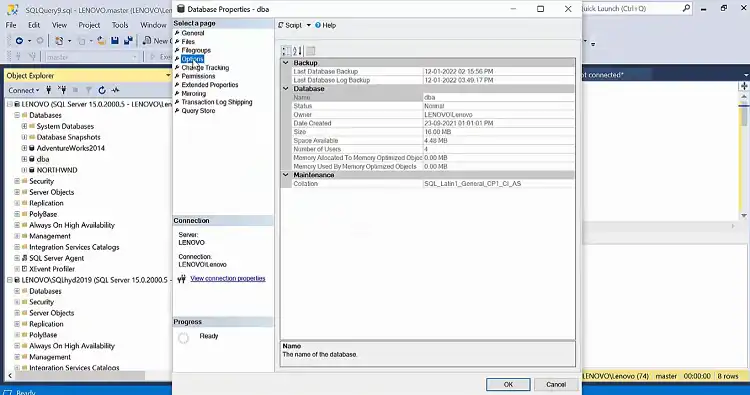
Step 5: Look for the “Encryption Enabled” property. If it’s set to “True,” then Transparent Data Encryption is enabled for the database.
Method 2: Using T-SQL Query
T-SQL can be also used to check for TDE:
USE master;GO
SELECT name, is_encryptedFROM sys.databases;Transparent Data Encryption is enabled for the database of interest if the “is_encrypted” column for that database is set to 1.
Checking Always Encrypted
Method 1: Using SQL Server Management Studio (SSMS)
Step 1: Use the proper credentials to log in to SQL Server Management Studio (SSMS).
Step 2: To see a list of the databases on the server, expand the “Databases” node in the Object Explorer.
Step 3: The database you want to check for Always Encrypted should be expanded.
Step 4: Locate the table with the encrypted columns by expanding the “Tables” node.
Step 5: Click the table with the right mouse button, then choose “Design.” You can see the columns’ characteristics in the table designer. If a column is encrypted with Always Encrypted, the “Encryption Type” property will be set to “Deterministic” or “Randomized.”
Method 2: Using T-SQL Query
The following T-SQL query can also be used to check for Always Encrypted columns:
USE YourDatabaseName;GO
SELECT SCHEMA_NAME(t.schema_id) + '.' + t.name AS TableName, c.name AS ColumnName, c.is_encrypted, c.encryption_type_descFROM sys.columns cJOIN sys.tables t ON c.object_id = t.object_idWHERE c.is_encrypted = 1;The table name, column name, encryption status, and encryption type are among the details that this query will return on encrypted columns in the specified database.
Frequently Asked Questions (FAQs)
1. Is It Possible to Have Encrypted and Unencrypted Databases on the Same SQL Server?
Answer: Yes, it is possible to have both encrypted and unencrypted databases on the same SQL Server. Transparent Data Encryption (TDE) allows selective encryption of specific databases while leaving others unencrypted based on security requirements.
2. What Is Transparent Data Encryption (TDE) In SQL Server, and How Does It Enhance Data Security?
Answer: Transparent Data Encryption (TDE) in SQL Server is a feature that automatically encrypts a database’s data and log files at rest. It enhances data security by protecting sensitive information stored on the disk, preventing unauthorized access to the data even if the physical storage media is compromised.
3. Does SQL Server provide any built-in features to rotate encryption keys?
Answer: Yes, SQL Server bolsters key rotation for both Transparent Data Encryption (TDE) and Cell-Level Encryption (CLE). Frequently turning encryption keys could be a great security practice to relieve potential dangers.
To Conclude
Checking database encryption in SQL Server is crucial in ensuring data security and compliance with data protection standards. Transparent Data Encryption (TDE) plays a vital role in this process, automatically encrypting the entire database at rest and in transit, safeguarding sensitive information from unauthorized access and potential data breaches.