How to Add IAM Role to EC2 Instance (4 Methods)
You can add an IAM role to an EC2 instance through the EC2 console, AWS CLI, or other options like Terraform and Amazon CloudFormation. Whether you like working with an easy GUI or prefer streamlined command lines, these approaches should work fine. Let’s have a closer look at how to add an IAM role to an EC2 instance using each method.
4 Methods of How to Add IAM Role to EC2 Instance
Below are the 4 methods of adding IAM role –
(A) How Do I Add IAM Role to EC2 Instance Using Console
Using the EC2 console is the easiest way of associating an IAM role with an EC2 instance. It includes the following five simple steps.
1. Open your Amazon EC2 Console.
2. Click on instances from the navigation menu.
3. Select the EC2 instance to which you want to add the IAM role.
4. Now, click Actions and choose Security.
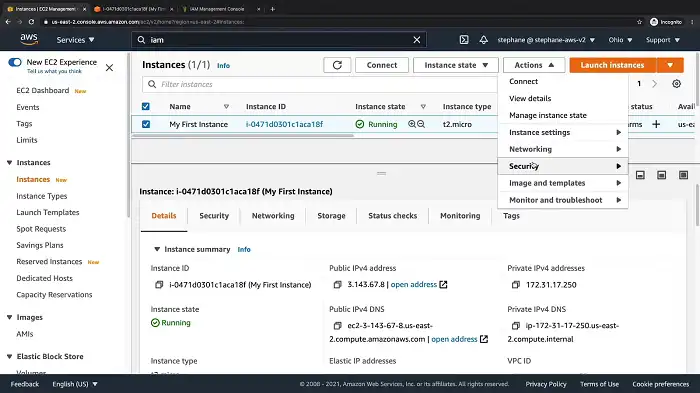
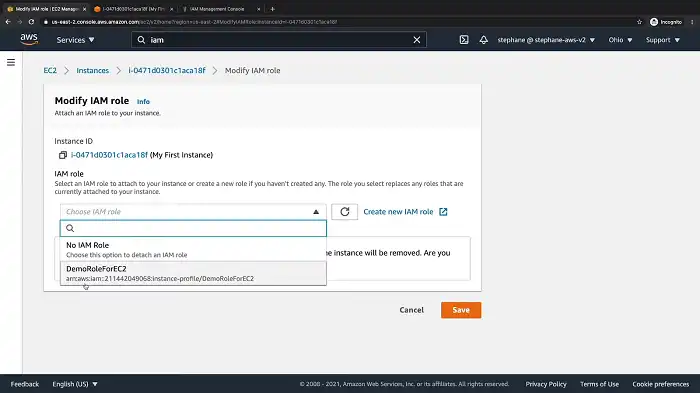
From the Security tab, select Modify IAM role.
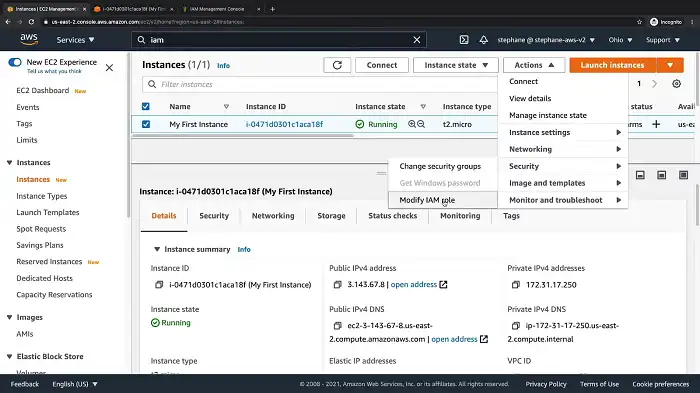
5. Select the IAM role you wish to add to the selected EC2 instance and click Save.
(B) How Do I Add IAM Role to EC2 Instance AWS CLI
You can also use AWS Command Line Interface (CLI) to add your IAM role to an EC2 instance. Here’s how.
1. Use the command below to get details about all your EC2 instances.
aws ec2 describe-instances
From the output, you can get the instance ID of the EC2 instance you want to add the IAM role to.
2. Next, run the following command to specify your desired instance profile and add the IAM role to it.
aws ec2 associate-iam-instance-profile \
–instance-id i-1234567890abcdef0 \
–iam-instance-profile Name=”TestRole-1″
To specify the instance profile, you can either enter its name directly or refer to the Amazon Resource Name (ARN). After running the command, the response may look like:
{
"IamInstanceProfileAssociation": {
"InstanceId": "i-1234567890abcdef0",
"State": "associating",
"AssociationId": "iip-assoc-0dbd8529a48294120",
"IamInstanceProfile": {
"Id": "AIPAJLNLDX3AMYZNWYYAY",
"Arn": "arn:aws:iam::123456789012:instance-profile/TestRole-1"
}
}
}(C) How Do I Attach an IAM Role to EC2 Instance CloudFormation?
Attaching an IAM role to the EC2 instance with CloudFormation requires you to associate the IamInstanceProfile with the template of your EC2 instance. These templates are generally in a JSON or YAML format.
Below are the steps involved in attaching an IAM role to an EC2 instance using a CloudFormation template.
1. Create an instance profile in the Resources section referring to the IAM role you want to add.
Resources:
MyInstanceProfile:
Type: 'AWS::IAM::InstanceProfile'
Properties:
Roles:
- IAMRoleName2. Add the instance profile you just created to the target EC2 instance by specifying the IamInstanceProfile property.
Resources:
MyEC2Instance:
Type: 'AWS::EC2::Instance'
Properties:
ImageId: ami-0abcdef1234567890
IamInstanceProfile: !Ref InstanceProfile3. After defining the template, create a CloudFormation stack that consists of resources manageable as separate units.
Go to the CloudFormation console and select Create Stack. Upload the template you created to add the IAM role to the EC2 instance you chose.
(D) How to Attach an IAM Role to an EC2 Instance Using Terraform?
Follow the steps below to attach an IAM role to an EC2 instance through Terraform.
1. Define the IAM role in the following manner.
provider "aws" {
region = "us-west-2" # Replace with your desired region
}
resource "aws_iam_role" "example_role" {
name = "example-iam-role"
assume_role_policy = jsonencode({
Version = "2012-10-17",
Statement = [
{
Effect = "Allow",
Principal = {
Service = "ec2.amazonaws.com" # Replace with the appropriate service or entity
},
Action = "sts:AssumeRole",
},
],
})
}
resource "aws_iam_policy" "example_policy" {
name = "example-iam-policy"
description = "An example IAM policy"
policy = jsonencode({
Version = "2012-10-17",
Statement = [
{
Effect = "Allow",
Action = "s3:GetObject",
Resource = "arn:aws:s3:::example-bucket/*", # Replace with your S3 bucket ARN
},
],
})
}In this example, the example-iam-role is defined with a trust policy allowing the EC2 service to assume the role. And the definition of example-iam-role allows the s3:GetObject actions within a specific S3 bucket. Replace the ARN with an actual bucket ARN. Lastly, the IAM policy gets attached to the IAM role.
2. Create an instance profile like the example below.
resource "aws_iam_role_policy_attachment" "example_attachment" {
policy_arn = aws_iam_policy.example_policy.arn
role = aws_iam_role.example_role.name
}3. Finally, launch an EC2 instance with the IAM role you just defined.
resource "aws_instance" "example_instance" {
ami = "ami-12345678" # Replace with the desired AMI ID
instance_type = "t2.micro" # Replace with the desired instance type
key_name = "example-key" # Replace with your EC2 key pair name
iam_instance_profile = aws_iam_role.example_role.name
tags = {
Name = "example-instance"
}
}FAQs (Frequently Asked Questions and Answers)
Can a new IAM role be granted to a running EC2 instance?
Although the preferred way is to assign a role to an instance during its launch, you can also grant an IAM role to a running EC2 instance.
Can we add multiple IAM roles to the EC2 instance?
AWS does not allow attaching more than one IAM role to an EC2 instance. An instance profile can contain only one IAM role.
How many IAM roles can be created in AWS?
According to the AWS documentation, you can create as many as 1000 IAM roles using a single AWS account.
Conclusion
In this article, we’ve explored different approaches for the integration between IAM roles and EC2 instances. Regardless of the method, always add only one IAM role to a particular EC2 instance. That way, you can avoid confusion while not compromising security.