In Depth Comparison of Security Issues: Public Vs Private Vs Hybrid Cloud Computing
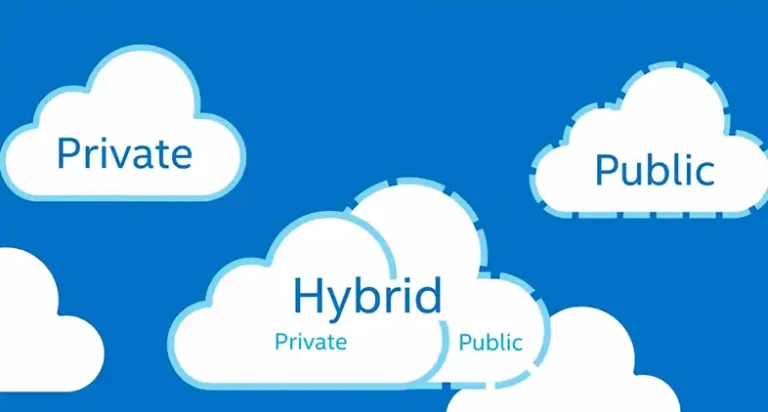
Security challenges in public clouds include external network vulnerability and shared resource risks, demanding careful vendor scrutiny. Private clouds face internal threats with a focus on robust network security, while hybrid clouds aim to secure connections between public and private components. Public clouds adhere to industry regulations, while private clouds manage internal compliance. Both face…